sysmaint - System Maintenance User
- Default Passwords
- Passwords
- Account Management
- Login
- Login Spoofing
- Safely Use Root Commands
sysmaintAccount- System Maintenance Panel
- Unrestricted Admin Mode
- Protection against Physical Attacks
- User Account Isolation (developers)
user-sysmaint-split (developers)- Polkit (formerly PolicyKit) /
pkexec - privleap /
leaprun

Sysmaint, or system maintenance, is an account created by the user-sysmaint-split feature. It increases security. Read about this new feature, how to use it and about our rationale on this page.
In case you are wondering how to fix:
permission denied: sudo
permission denied: pkexec
Screenshot
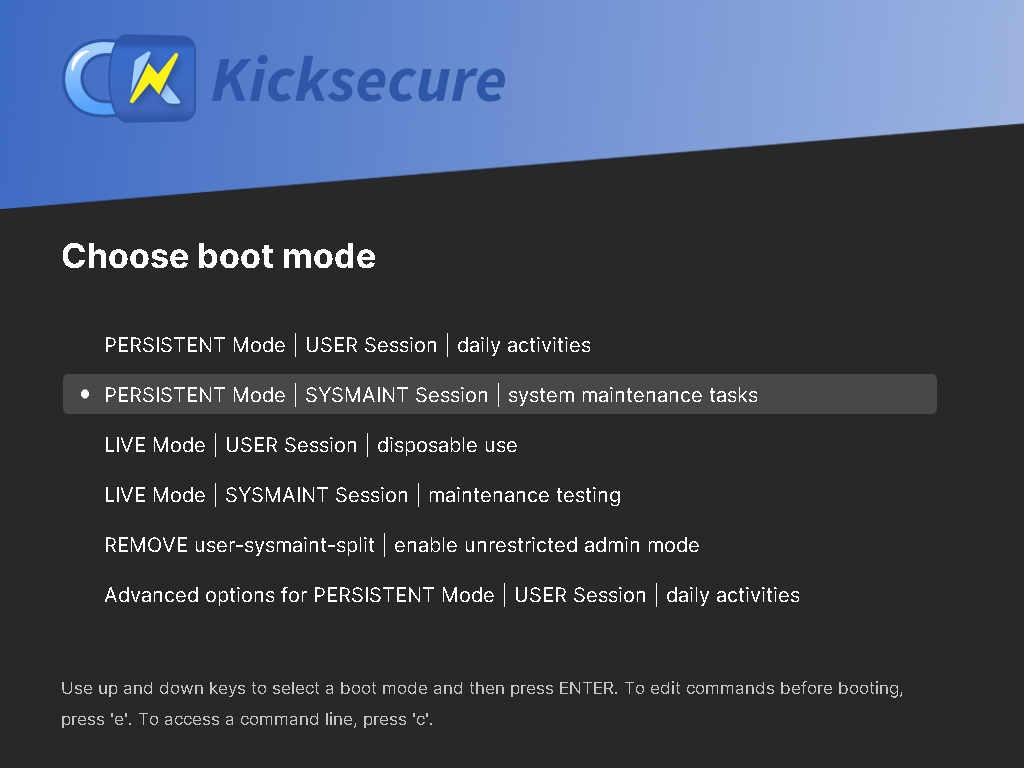
[edit]Image: Kicksecure - sysmaint Boot Option in GRUB Boot Menu
Overview: What is sysmaint and Why Should I Care?
[edit]Starting from version 17.3.9.9, Kicksecure comes with a security feature called user-sysmaint-split enabled by default (in LXQt and above). This feature creates two separate user accounts:
user- for daily activities like browsing, writing documents, etc.sysmaint- short for system maintenance; used for tasks that require administrative rights such as installing or updating software.
This separation improves security. For example, if malware compromises your web browser in the user session, it won't have permission to make critical system changes or install rootkits (malicious software that can hide in the system).
You only use the sysmaint account when you want to change system behavior - such as adding new programs, applying updates, or performing administrative tasks.
The opposite of user-sysmaint-split is Unrestricted Admin Mode, which allows the user account to use administrative tools like sudo, su, lxsudo, pkexec directly. This is less secure and not enabled by default, but it can be configured if it better suits your use case.
Real-World Example Use Cases
[edit]- You want to install a new application:
- Reboot into the
sysmaintaccount to perform the installation. - Once done, reboot back into your regular desktop account.
- Reboot into the
- You want to install system updates:
- Boot into
sysmaintmode and run the updates from the System Maintenance Panel.
- Boot into
- You want to avoid malware affecting system settings:
- Use your regular
useraccount for browsing and daily work. Since it doesn’t have admin access, it's harder for malware to deeply damage your system.
- Use your regular
Default Installation Status
[edit]- Old versions: Kicksecure build version up to version
17.2.8.5will not automatically includeuser-sysmaint-split. However, users can choose to install it manually (see #Installation). It will likely be included by default when upgrading to a new major version (e.g., version18). - New versions:
- host: Includes
user-sysmaint-splitby default. - command line interface (CLI): The
kicksecure-host-climeta package does not includeuser-sysmaint-splitby default. - servers:
user-sysmaint-splitis not installed by default on servers. - Distribution Morphing: Not installed by default. Will be installed by default for GUI version starting from version
18.
- host: Includes
Version Overview
[edit]graphical user interface (GUI) versus command line interface (CLI).
| Feature | Kicksecure LXQt (GUI) | Kicksecure CLI |
|---|---|---|
user-sysmaint-split
|
Yes, installed by default in new images. | No, not installed by default. |
| Old Versions | No, will not be automatically installed during the Kicksecure 17 release cycle to avoid breaking existing user workflows.
|
No, not applicable, will remain sudo passwordless by default.
|
| New Images | Yes, will come with user-sysmaint-split installed by default.
|
No, user-sysmaint-split will not be included.
|
| Release Upgrade | Under consideration. | No, user-sysmaint-split will not be included.
|
| Opt-Out | Yes, supported via Unrestricted Admin Mode. | Yes |
| Opt-In | Yes, user-sysmaint-split can be installed at any time.
|
Yes |
Installation
[edit]Install package(s) user-sysmaint-split sysmaint-panel following these instructions
1 Platform specific notice.
- Kicksecure: No special notice.
- Kicksecure-Qubes: In Template.
2 Update the package lists and upgrade the system.
sudo apt update && sudo apt full-upgrade
3 Install the user-sysmaint-split sysmaint-panel package(s).
Using apt command line --no-install-recommends option is in most cases optional.
sudo apt install --no-install-recommends user-sysmaint-split sysmaint-panel
4 Platform specific notice.
- Kicksecure: No special notice.
- Kicksecure-Qubes: Shut down Template and restart App Qubes based on it as per Qubes Template Modification.
5 Done.
The procedure of installing package(s) user-sysmaint-split sysmaint-panel is complete.
Usage
[edit]1 Platform specific.
Select your platform.
Kicksecure
When user-sysmaint-split is installed, the account user will no longer be able to use privilege escalation tools (sudo, su, pkexec) when logged into any account other than sysmaint.
This change takes effect immediately.
To perform system maintenance tasks such as checking for software updates, installing updates, etc, the user will have to reboot into the sysmaint account. To do this, restart the system normally, then select PERSISTENT Mode | SYSMAINT Session | system maintenance tasks from the boot menu.
Figure: Persistent Mode - Sysmaint Session - GRUB Boot Menu Option
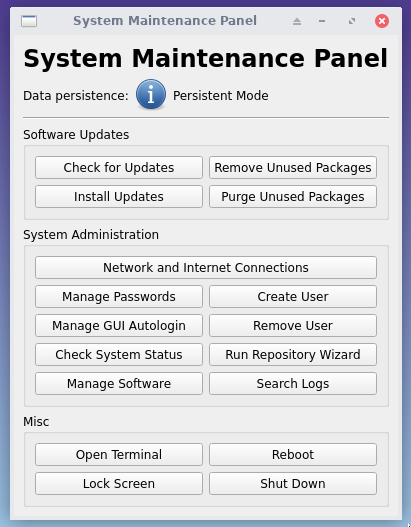
The system will boot into a minimal desktop session with the System Maintenance Panel running.
Figure: System Maintenance Panel
To reduce attack surface, most superfluous background services are suppressed while booted into the sysmaint account.
The sysmaint desktop session is intentionally minimal and not suited for normal desktop use. This is to discourage using it for work that has a higher risk of causing a difficult-to-avoid system compromise (such as web browsing). Quick shortcuts are provided for simple software management and system administration tasks, while more advanced tasks can be performed from a terminal. The sudo and pkexec commands will be usable here.
Once you are done with system maintenance tasks, click "Reboot" to reboot the system. Then boot into PERSISTENT Mode | USER Session | daily activities or LIVE Mode | USER Session | disposable use. This will provide you with a standard desktop session.
When booted in PERSISTENT Mode | SYSMAINT Session | system maintenance tasks, you can also log into the sysmaint account from a virtual consoles (tty). Simply input the account name sysmaint at the login prompt. This session behaves identically to a typical virtual console session. A short informational message will be printed after login reminding you that the sysmaint account must be used with caution.
Kicksecure for Qubes
2 Qubes version specific.
Select your Qubes version.
Qubes R4.2
In Qubes OS R4.2 and earlier: Kicksecure for Qubes cannot be booted into sysmaint session. However, user-sysmaint-split is useful in Qubes VMs too because it makes SUID privilege escalation tools (sudo, su, pkexec) inaccessible for account user. You can access the root account by opening a Qubes Root Console.
Qubes R4.3
Qubes OS R4.3 and later:
- Boot modes support: Support boot modes

.
- Usage of boot modes: Kicksecure for Qubes uses these to allow Kicksecure any Qube to be booted in either
PERSISTENT Mode | USER Session | daily activitiesorPERSISTENT Mode | SYSMAINT Session | system maintenance tasks.
- Usage of boot modes: Kicksecure for Qubes uses these to allow Kicksecure any Qube to be booted in either
- Template:
kicksecure-18Template will boot inPERSISTENT Mode | SYSMAINT Session | system maintenance tasks. - App Qubes:
KicksecureApp Qubes and Disposables will boot inPERSISTENT Mode | USER Session | daily activities. - Comparison with non-Qubes:
PERSISTENT Mode | USER Session | daily activitiesandPERSISTENT Mode | SYSMAINT Session | system maintenance tasksare mostly functionally identical under Qubes OS.PERSISTENT Mode | SYSMAINT Session | system maintenance tasksdiffers in the following ways:- The default user account for most actions is changed to
sysmaint. - User-specific system services such as the X11 server run as account
sysmaint. - Potentially dangerous operations such as opening URLs are disabled.
- The System Maintenance Panel is usable.
- Privilege escalation tools are easily usable, since the
sysmaintaccount will be provided rather than theuseraccount.
It is possible to boot a Kicksecure Qube in a non-standard boot mode (i.e. booting a Template in PERSISTENT Mode | USER Session | daily activities, or booting an AppVM in PERSISTENT Mode | SYSMAINT Session | system maintenance tasks). To do so, change the boot mode of the Qube before starting it.
1. Ensure the Qube is shut down.
2. Open Qube Manager.
Start menu → Gear icon → Qubes Tools → Qube Manager
3. Click on the VM you wish to change the boot mode of.
4. Click "Settings" in the toolbar.
5. Click the "Advanced" tab in the Settings window.
6. In the "Kernel" section, change "Boot mode" to your desired boot mode.
7. Click "OK" in the Settings window.
8. Start the Qube. It will boot in the selected boot mode.
9. Done.
The procedure of switching the boot mode for a Qube is now complete.
Fast User Switching
[edit]Platform specific. Select your platform.
Kicksecure
Reboot into sysmaint session is required, as documented above.
Note: It is unsupported to switch from account user to sysmaint using:
- Start Menu → logout
- Start Menu → switch user
This is a security feature. [1]
Running services in sysmaint sessions
[edit]When booted in PERSISTENT Mode | SYSMAINT Session | system maintenance tasks, only the minimum services needed for the session to be usable are started by default. New services are prevented from automatically starting during APT software upgrades.
While enabling additional services within the sysmaint session is generally discouraged, it may be necessary in some situations. Services can be started either temporarily for one sysmaint session, or persistently for all sysmaint sessions.
To start a service for the current sysmaint session:
Note: Replace service-name in the below steps with the name of the service you are starting. For instance, if you are configuring openvpn.service, replace all instances of service-name with openvpn.
1. Open a terminal by clicking Open Terminal in the System Maintenance Panel.
2. Type sudo systemctl start service-name.service
3. Done.
The procedure of starting a service for one sysmaint session is complete.
To enable a service persistently, so that it autostarts on every sysmaint session boot:
Note: Replace service-name in the below steps with the name of the service you are configuring. For instance, if you are configuring openvpn.service, replace all instances of service-name with openvpn.
1. Open a terminal by clicking Open Terminal in the System Maintenance Panel.
2. Navigate to the directory containing the systemd unit for to the service you wish to enable. Usually, this will be /usr/lib/systemd/system or /etc/systemd/systemd.
3. Create a new configuration directory for the service by running sudo mkdir -p service-name.service.d.
4. Enter the directory you just created by running cd service-name.service.d.
5. Create a new configuration file for the service by running sudo nano 99_sysmaint-enable.conf.
6. Type the following lines into the configuration file:
[Install] WantedBy=sysmaint-boot.target
7. Press Ctrl+S to save the file, then press Ctrl+X to exit the text editor.
8. Reload systemd unit configuration files by running sudo systemctl daemon-reload.
9. Fully enable the service by running sudo systemctl enable service-name.service.
10. Ensure the systemctl enable command output the following notice. If you see this, it indicates that the service has been successfully enabled.
Created symlink /etc/systemd/system/sysmaint-boot.target.wants/service-name.service → /lib/systemd/system/service-name.service.
11. Start the service in the current sysmaint session by running sudo systemctl start service-name.service.
12. Done.
The procedure of persistently enabling and starting a service in sysmaint session is now complete.
Notes
[edit]-
sysmaintaccount restrictions: Several restrictions are imposed to reduce the risk of thesysmaintaccount becoming compromised:- Locked access depending on boot mode: The
sysmaintaccount is locked and cannot be logged into when booted into modes other thanPERSISTENT Mode | SYSMAINT Session | system maintenance tasks. - Session limitation: Logging into the
sysmaintaccount using anything other than the specialsysmaintdesktop session is prohibited. - Discouragement of other logins: When booted in
PERSISTENT Mode | SYSMAINT Session | system maintenance tasks, you will be discouraged (but not entirely prevented) from logging into accounts other thansysmaint. Locking accounts such as accountuseris not implemented, since doing so would make it very tricky or even impossible for the user to permanently lock accounts themselves. - Inhibition of non-critical services: When booted in
PERSISTENT Mode | SYSMAINT Session | system maintenance tasks, only the minimum services needed for the session to be usable are started by default. New services are prevented from automatically starting during APT software upgrades.
- Locked access depending on boot mode: The
Questions and Answers
[edit]- Why is there a separate
sysmaintaccount?
- Why is it required to boot into
sysmaintmode, why not simply use start menu → switch user? (Fast User Switching)- This is to mitigate login spoofing attacks and to to prevent
sudopassword sniffing.
- This is to mitigate login spoofing attacks and to to prevent
- How to go back to unrestricted admin mode, where account
usercan usesudo?- See #Uninstallation.
user-sysmaint-split - GUI vs CLI - Default Installation Status Differences
[edit]user-sysmaint-split is different for the graphical user interface (GUI) versus the command line interface (CLI) version.
In the future, the CLI version will be improved to be more suitable for servers.
Server support for user-sysmaint-split, however, isn't as sophisticated yet as it is for the GUI version. For some server use cases, user-sysmaint-split may be less needed or unneeded. This topic is elaborated in the development chapter user-sysmaint-split Server Support.
Applications requiring Administrative Rights during User Session
[edit]If it is unsuitable to run some applications in the sysmaint session, then this could be difficult. This is because historically, Freedom Software Linux desktop distributions did not have a strong user-sysmaint-split.
There might be many cases where applications should be run in the user session, but this is not possible because some aspect of the application requires administrative ("root") rights.
Options:
- A)
privleapcustom actions: If it's possible to do this on the command line interface (CLI), Advanced Users could consider configuring privleap custom actions. - B) Unrestricted admin mode: This mode disables the separation between the user and system maintenance roles, allowing the user to directly perform administrative tasks without needing to switch contexts. It provides more flexibility for tasks requiring elevated privileges but at the cost of reduced compartmentalization and security. This approach might be more suitable in environments where usability or workflow requirements outweigh the benefits of strict privilege separation. See Uninstalling user-sysmaint-split and Enabling Unrestricted Admin Mode.
- C) Use multiple virtual machines (VM): For compartmentalization. Select VMs that require administrative ("
root") rights could use unrestricted admin mode. Others could keepuser-sysmaint-split.
Issues:
- ZuluCrypt not working in user session

- Veracrypt containers do not open

- Struggling with the point release update - user-sysmaint-split - sudo

Advanced Topics
[edit]For Advanced Users.
enable sudo access in USER session
[edit]1 Warnings.
- For debugging or advanced users only.
- Enabling
sudoaccess during USER session can be a security issue. - This is often unnecessary. Uninstallation of the
user-sysmaint-splitpackage might be better.
2 Boot into PERSISTENT Mode | SYSMAINT Session | system maintenance tasks.
Setting this up requires booting into sysmaint session.
3 Create file /etc/privleap/conf.d/privleap-debugging.conf.
sudo append-once /etc/privleap/conf.d/privleap-debugging.conf "\ [action:sudo] Command=chmod o+x /usr/bin/sudo #Command=/usr/libexec/helper-scripts/sudo-tools-enable AuthorizedGroups=sudo AuthorizedUsers=user "
4 Boot into PERSISTENT Mode | USER Session | daily activities.
5 Enable sudo.
leaprun sudo
6 Notice.
Above command can be run whenever required to enable sudo.
sudo access will be automatically disabled after installing or removing a package using APT. This is because this triggers SUID Disabler and Permission Hardener, which will re-disable sudo, unless an /etc/permission-hardener.d configuration folder snippet gets added.
7 Use of sudo.
sudo can be used normally. For example:
sudo touch /etc/testfile
8 Done.
The process is complete.
Uninstallation
[edit]See Uninstalling user-sysmaint-split and enabling Unrestricted Admin Mode.
Known Issues
[edit]- Qubes has potential local privilege escalation issue: harden insecure permissions inside
/dev/xenfolder / research security impact of the Qubes/dev/xenfolder permissions #9717
-- This issue is unspecific to Kicksecure and is entirely unrelated to Kicksecure. It equally applies to App Qubes that are not using
qubes-core-agent-passwordless-rootsuch as Qubes Debian minimal Template.
Developers
[edit]- User Account Isolation (developers)
user-sysmaint-split (developers)- Kicksecure GitHub user-sysmaint-split repository
- Kicksecure GitHub sysmaint-panel repository
Footnotes
[edit]

We believe security software like Kicksecure needs to remain Open Source and independent. Would you help sustain and grow the project? Learn more about our 13 year success story and maybe DONATE!