Troubleshooting

The wiki page covers troubleshooting tips for installation issues, general issues, network issues and hardware problems.
Contents
ISO[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#ISO
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#ISO|ISO]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#ISO|ISO]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[ISO](https://www.kicksecure.com/wiki/Troubleshooting#ISO)
Click = Copy
Copied to clipboard!
[ISO](https://www.kicksecure.com/wiki/Troubleshooting#ISO)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[ISO](https://www.kicksecure.com/wiki/Troubleshooting#ISO)
Click = Copy
Copied to clipboard!
[ISO](https://www.kicksecure.com/wiki/Troubleshooting#ISO)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#ISO]ISO[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#ISO]ISO[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
ISO to USB Image Writer Tools[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#ISO_to_USB_Image_Writer_Tools
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#ISO_to_USB_Image_Writer_Tools|ISO to USB Image Writer Tools]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#ISO_to_USB_Image_Writer_Tools|ISO to USB Image Writer Tools]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[ISO to USB Image Writer Tools](https://www.kicksecure.com/wiki/Troubleshooting#ISO_to_USB_Image_Writer_Tools)
Click = Copy
Copied to clipboard!
[ISO to USB Image Writer Tools](https://www.kicksecure.com/wiki/Troubleshooting#ISO_to_USB_Image_Writer_Tools)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[ISO to USB Image Writer Tools](https://www.kicksecure.com/wiki/Troubleshooting#ISO_to_USB_Image_Writer_Tools)
Click = Copy
Copied to clipboard!
[ISO to USB Image Writer Tools](https://www.kicksecure.com/wiki/Troubleshooting#ISO_to_USB_Image_Writer_Tools)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#ISO_to_USB_Image_Writer_Tools]ISO to USB Image Writer Tools[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#ISO_to_USB_Image_Writer_Tools]ISO to USB Image Writer Tools[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
functional, bootable image:
- Flashing using a Qubes Kicksecure VM with hide hardware information enabled using
cp - Flashing using a Qubes Kicksecure VM using KDE ISO Image Writer from Flathub
- Flashing using a Debian VM balanaEtcher AppImage.
- Flashing using a Windows OS with balanaEtcher installer version.
- Flashing using a Windows OS with UNetbootin (portable).
broken:
- Flashing using a Qubes Kicksecure VM with hide hardware information enabled using balanaEtcher, which shows an error message due to hide hardware information.
Tips[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#Tips
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#Tips|Tips]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#Tips|Tips]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[Tips](https://www.kicksecure.com/wiki/Troubleshooting#Tips)
Click = Copy
Copied to clipboard!
[Tips](https://www.kicksecure.com/wiki/Troubleshooting#Tips)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[Tips](https://www.kicksecure.com/wiki/Troubleshooting#Tips)
Click = Copy
Copied to clipboard!
[Tips](https://www.kicksecure.com/wiki/Troubleshooting#Tips)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Tips]Tips[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Tips]Tips[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
- Exercise on separate notebook.
- Use a VM to flash for security against data loss.
Live ISO Known Issues[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#Live_ISO_Known_Issues
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#Live_ISO_Known_Issues|Live ISO Known Issues]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#Live_ISO_Known_Issues|Live ISO Known Issues]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[Live ISO Known Issues](https://www.kicksecure.com/wiki/Troubleshooting#Live_ISO_Known_Issues)
Click = Copy
Copied to clipboard!
[Live ISO Known Issues](https://www.kicksecure.com/wiki/Troubleshooting#Live_ISO_Known_Issues)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[Live ISO Known Issues](https://www.kicksecure.com/wiki/Troubleshooting#Live_ISO_Known_Issues)
Click = Copy
Copied to clipboard!
[Live ISO Known Issues](https://www.kicksecure.com/wiki/Troubleshooting#Live_ISO_Known_Issues)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Live_ISO_Known_Issues]Live ISO Known Issues[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Live_ISO_Known_Issues]Live ISO Known Issues[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
balenaEtcher[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#balenaEtcher
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#balenaEtcher|balenaEtcher]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#balenaEtcher|balenaEtcher]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[balenaEtcher](https://www.kicksecure.com/wiki/Troubleshooting#balenaEtcher)
Click = Copy
Copied to clipboard!
[balenaEtcher](https://www.kicksecure.com/wiki/Troubleshooting#balenaEtcher)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[balenaEtcher](https://www.kicksecure.com/wiki/Troubleshooting#balenaEtcher)
Click = Copy
Copied to clipboard!
[balenaEtcher](https://www.kicksecure.com/wiki/Troubleshooting#balenaEtcher)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#balenaEtcher]balenaEtcher[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#balenaEtcher]balenaEtcher[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
Platform specific.
- A) Non-Windows host operating systems such as macOS or Linux: No special notice.
- B) Windows: See below.
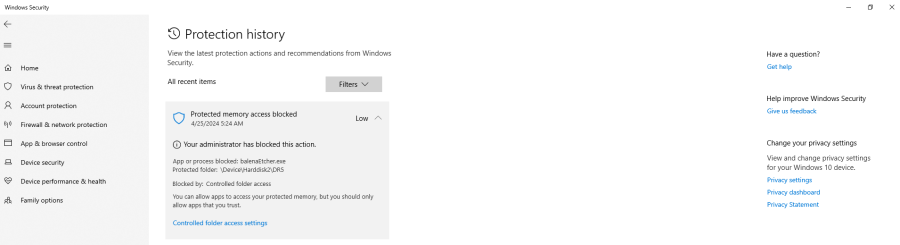
If you have Controlled Folder Access![]()
enabled, you need to allow changes by Etcher:
Figure: Windows Protection History
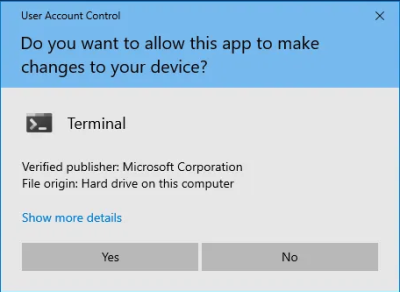
If you have User Account Control![]()
enabled, allow Etcher to make changes to your device by pressing "Yes" when a popup similar to the following appears:
Figure: Windows User Account Control
KDE ISO Image Writer[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#KDE_ISO_Image_Writer
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#KDE_ISO_Image_Writer|KDE ISO Image Writer]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#KDE_ISO_Image_Writer|KDE ISO Image Writer]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[KDE ISO Image Writer](https://www.kicksecure.com/wiki/Troubleshooting#KDE_ISO_Image_Writer)
Click = Copy
Copied to clipboard!
[KDE ISO Image Writer](https://www.kicksecure.com/wiki/Troubleshooting#KDE_ISO_Image_Writer)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[KDE ISO Image Writer](https://www.kicksecure.com/wiki/Troubleshooting#KDE_ISO_Image_Writer)
Click = Copy
Copied to clipboard!
[KDE ISO Image Writer](https://www.kicksecure.com/wiki/Troubleshooting#KDE_ISO_Image_Writer)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#KDE_ISO_Image_Writer]KDE ISO Image Writer[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#KDE_ISO_Image_Writer]KDE ISO Image Writer[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
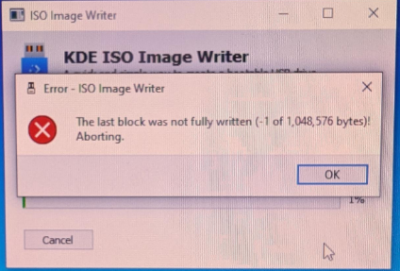
The last block was not fully written (-1 of 1,048,576 bytes)!KDE ISO Image Writer Error Message
In this case,
- A) try to unmount the USB device first or
- B) use a different ISO Image Writer tool.
DVD Support[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#DVD_Support
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#DVD_Support|DVD Support]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#DVD_Support|DVD Support]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[DVD Support](https://www.kicksecure.com/wiki/Troubleshooting#DVD_Support)
Click = Copy
Copied to clipboard!
[DVD Support](https://www.kicksecure.com/wiki/Troubleshooting#DVD_Support)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[DVD Support](https://www.kicksecure.com/wiki/Troubleshooting#DVD_Support)
Click = Copy
Copied to clipboard!
[DVD Support](https://www.kicksecure.com/wiki/Troubleshooting#DVD_Support)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#DVD_Support]DVD Support[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#DVD_Support]DVD Support[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.

Untested. Should work in theory. Tested inside QEMU and VirtualBox with an emulated CD-ROM drive. So chances are good that it would work with a real DVD drive as well.
Dual Boot[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#Dual_Boot
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#Dual_Boot|Dual Boot]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#Dual_Boot|Dual Boot]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[Dual Boot](https://www.kicksecure.com/wiki/Troubleshooting#Dual_Boot)
Click = Copy
Copied to clipboard!
[Dual Boot](https://www.kicksecure.com/wiki/Troubleshooting#Dual_Boot)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[Dual Boot](https://www.kicksecure.com/wiki/Troubleshooting#Dual_Boot)
Click = Copy
Copied to clipboard!
[Dual Boot](https://www.kicksecure.com/wiki/Troubleshooting#Dual_Boot)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Dual_Boot]Dual Boot[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Dual_Boot]Dual Boot[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
It is recommended to physically disconnect any other physical disks while installing Kicksecure (or any other operating system) to mitigate the risk of the installer overwriting the wrong drive due to user error or software bugs.
Fastboot[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#Fastboot
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#Fastboot|Fastboot]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#Fastboot|Fastboot]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[Fastboot](https://www.kicksecure.com/wiki/Troubleshooting#Fastboot)
Click = Copy
Copied to clipboard!
[Fastboot](https://www.kicksecure.com/wiki/Troubleshooting#Fastboot)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[Fastboot](https://www.kicksecure.com/wiki/Troubleshooting#Fastboot)
Click = Copy
Copied to clipboard!
[Fastboot](https://www.kicksecure.com/wiki/Troubleshooting#Fastboot)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Fastboot]Fastboot[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Fastboot]Fastboot[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
Fastboot is a BIOS setting which skips attempting to boot from USB on some computers. In this case, the user must disable Fastboot in order to be able to boot from USB.
Encryption Settings[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#Encryption_Settings
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#Encryption_Settings|Encryption Settings]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#Encryption_Settings|Encryption Settings]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[Encryption Settings](https://www.kicksecure.com/wiki/Troubleshooting#Encryption_Settings)
Click = Copy
Copied to clipboard!
[Encryption Settings](https://www.kicksecure.com/wiki/Troubleshooting#Encryption_Settings)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[Encryption Settings](https://www.kicksecure.com/wiki/Troubleshooting#Encryption_Settings)
Click = Copy
Copied to clipboard!
[Encryption Settings](https://www.kicksecure.com/wiki/Troubleshooting#Encryption_Settings)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Encryption_Settings]Encryption Settings[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Encryption_Settings]Encryption Settings[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
- Default Encryption Settings: Which encryption settings will be used? See: Click = Copy Copied to clipboard! cryptsetup luksFormat --help
- Authority: Where are the default encryption settings coming from? From distribution defaults. In this case, from Debian because Kicksecure is based on Debian.
- User customization: No, unfortunately not possible. Full disk encryption settings are not configurable in calamares. calamares upstream bug report

(closed, but not implemented, "patches welcome")
- Alternatives: Distribution Morphing: morphing Debian into Kicksecure
- Forum discussion: ISO - cryptsetup Full Disk Encryption (FDE) - set more secure default encryption settings

Minor Issues[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#Minor_Issues
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#Minor_Issues|Minor Issues]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#Minor_Issues|Minor Issues]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[Minor Issues](https://www.kicksecure.com/wiki/Troubleshooting#Minor_Issues)
Click = Copy
Copied to clipboard!
[Minor Issues](https://www.kicksecure.com/wiki/Troubleshooting#Minor_Issues)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[Minor Issues](https://www.kicksecure.com/wiki/Troubleshooting#Minor_Issues)
Click = Copy
Copied to clipboard!
[Minor Issues](https://www.kicksecure.com/wiki/Troubleshooting#Minor_Issues)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Minor_Issues]Minor Issues[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Minor_Issues]Minor Issues[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
This might be an issue while installing additional packages while running the live ISO. This will not be an issue after installing to hard drive.
Failed to mount sysroot.mount - /sysroot.[edit]
The message Failed to mount sysroot.mount - /sysroot. during the boot ISO process is only a cosmetic issue. It can be safely ignored.
This issue will be fixed in Kicksecure 18 and above (Debian trixie based).
Details here: https://forums.kicksecure.com/t/iso-error-message-during-boot-mount-sysroot-special-device-liveos-rootfs-does-not-exist/418![]()
update-grub[edit]
Note: There is most likely no need to run the following command. This is only documentation "what if". If running the following command,
sudo update-grub
then the following error message would be shown.
/usr/sbin/grub-probe: error: failed to get canonical path of `LiveOS_rootfs'. zsh: exit 1 sudo update-grub
Please report a bug if this breaks something for you. Adding a workaround for this would not be difficult.
This command is also unrelated to fixing installation issues. Users executing update-grub from an ISO is not very useful because an ISO is a read-only filesystem. Running update-grub can be useful during the installation from ISO to hard drive, but this is something that needs to happen inside a chroot, which is a specifically prepared environment. This is very difficult for most users and unnecessary because this is part of the tasks of the installer.
Calamares ISO Installer[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#Calamares_ISO_Installer
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#Calamares_ISO_Installer|Calamares ISO Installer]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#Calamares_ISO_Installer|Calamares ISO Installer]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[Calamares ISO Installer](https://www.kicksecure.com/wiki/Troubleshooting#Calamares_ISO_Installer)
Click = Copy
Copied to clipboard!
[Calamares ISO Installer](https://www.kicksecure.com/wiki/Troubleshooting#Calamares_ISO_Installer)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[Calamares ISO Installer](https://www.kicksecure.com/wiki/Troubleshooting#Calamares_ISO_Installer)
Click = Copy
Copied to clipboard!
[Calamares ISO Installer](https://www.kicksecure.com/wiki/Troubleshooting#Calamares_ISO_Installer)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Calamares_ISO_Installer]Calamares ISO Installer[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Calamares_ISO_Installer]Calamares ISO Installer[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
Connectivity Troubleshooting[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#Connectivity_Troubleshooting
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#Connectivity_Troubleshooting|Connectivity Troubleshooting]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#Connectivity_Troubleshooting|Connectivity Troubleshooting]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[Connectivity Troubleshooting](https://www.kicksecure.com/wiki/Troubleshooting#Connectivity_Troubleshooting)
Click = Copy
Copied to clipboard!
[Connectivity Troubleshooting](https://www.kicksecure.com/wiki/Troubleshooting#Connectivity_Troubleshooting)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[Connectivity Troubleshooting](https://www.kicksecure.com/wiki/Troubleshooting#Connectivity_Troubleshooting)
Click = Copy
Copied to clipboard!
[Connectivity Troubleshooting](https://www.kicksecure.com/wiki/Troubleshooting#Connectivity_Troubleshooting)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Connectivity_Troubleshooting]Connectivity Troubleshooting[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Connectivity_Troubleshooting]Connectivity Troubleshooting[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
ICMP Fix[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#ICMP_Fix
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#ICMP_Fix|ICMP Fix]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#ICMP_Fix|ICMP Fix]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[ICMP Fix](https://www.kicksecure.com/wiki/Troubleshooting#ICMP_Fix)
Click = Copy
Copied to clipboard!
[ICMP Fix](https://www.kicksecure.com/wiki/Troubleshooting#ICMP_Fix)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[ICMP Fix](https://www.kicksecure.com/wiki/Troubleshooting#ICMP_Fix)
Click = Copy
Copied to clipboard!
[ICMP Fix](https://www.kicksecure.com/wiki/Troubleshooting#ICMP_Fix)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#ICMP_Fix]ICMP Fix[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#ICMP_Fix]ICMP Fix[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
Therefore no such fix required yet.
Qubes-specific Connectivity Issue[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#Qubes-specific_Connectivity_Issue
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#Qubes-specific_Connectivity_Issue|Qubes-specific Connectivity Issue]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#Qubes-specific_Connectivity_Issue|Qubes-specific Connectivity Issue]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[Qubes-specific Connectivity Issue](https://www.kicksecure.com/wiki/Troubleshooting#Qubes-specific_Connectivity_Issue)
Click = Copy
Copied to clipboard!
[Qubes-specific Connectivity Issue](https://www.kicksecure.com/wiki/Troubleshooting#Qubes-specific_Connectivity_Issue)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[Qubes-specific Connectivity Issue](https://www.kicksecure.com/wiki/Troubleshooting#Qubes-specific_Connectivity_Issue)
Click = Copy
Copied to clipboard!
[Qubes-specific Connectivity Issue](https://www.kicksecure.com/wiki/Troubleshooting#Qubes-specific_Connectivity_Issue)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Qubes-specific_Connectivity_Issue]Qubes-specific Connectivity Issue[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Qubes-specific_Connectivity_Issue]Qubes-specific Connectivity Issue[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
Complete the following steps:
- Shut down
kicksecure. - Change the
kicksecureNetVM setting fromsys-firewalltosys-net. - Restart
kicksecure.
This procedure might help, but should not be considered a final solution. [2]
Why can't I Ping the Kicksecure?[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#Why_can.27t_I_Ping_the_Kicksecure.3F
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#Why_can.27t_I_Ping_the_Kicksecure.3F|Why can't I Ping the Kicksecure?]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#Why_can.27t_I_Ping_the_Kicksecure.3F|Why can't I Ping the Kicksecure?]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[Why can't I Ping the Kicksecure?](https://www.kicksecure.com/wiki/Troubleshooting#Why_can.27t_I_Ping_the_Kicksecure.3F)
Click = Copy
Copied to clipboard!
[Why can't I Ping the Kicksecure?](https://www.kicksecure.com/wiki/Troubleshooting#Why_can.27t_I_Ping_the_Kicksecure.3F)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[Why can't I Ping the Kicksecure?](https://www.kicksecure.com/wiki/Troubleshooting#Why_can.27t_I_Ping_the_Kicksecure.3F)
Click = Copy
Copied to clipboard!
[Why can't I Ping the Kicksecure?](https://www.kicksecure.com/wiki/Troubleshooting#Why_can.27t_I_Ping_the_Kicksecure.3F)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Why_can.27t_I_Ping_the_Kicksecure.3F]Why can't I Ping the Kicksecure?[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Why_can.27t_I_Ping_the_Kicksecure.3F]Why can't I Ping the Kicksecure?[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
The Kicksecure does not respond to ping or similar commands because it is firewalled for security reasons; see /usr/bin/kicksecure_firewall or refer to the Kicksecure source code. In most cases it is unnecessary to ping the Kicksecure anyhow.
If you insist on pinging the Kicksecure or have a unique setup that requires it, then this can be tested by clearing all firewall rules with the dev_clearnet
![]()
script. Alternatively, a script can be run to try and unload / remove every iptables rule, or the Kicksecure firewall can be hacked to not load at all. The latter method is only for experts and it is necessary to comment out exit 0 at the beginning.
General Troubleshooting[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#General_Troubleshooting
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#General_Troubleshooting|General Troubleshooting]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#General_Troubleshooting|General Troubleshooting]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[General Troubleshooting](https://www.kicksecure.com/wiki/Troubleshooting#General_Troubleshooting)
Click = Copy
Copied to clipboard!
[General Troubleshooting](https://www.kicksecure.com/wiki/Troubleshooting#General_Troubleshooting)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[General Troubleshooting](https://www.kicksecure.com/wiki/Troubleshooting#General_Troubleshooting)
Click = Copy
Copied to clipboard!
[General Troubleshooting](https://www.kicksecure.com/wiki/Troubleshooting#General_Troubleshooting)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#General_Troubleshooting]General Troubleshooting[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#General_Troubleshooting]General Troubleshooting[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
Introduction[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#Introduction
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#Introduction|Introduction]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#Introduction|Introduction]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[Introduction](https://www.kicksecure.com/wiki/Troubleshooting#Introduction)
Click = Copy
Copied to clipboard!
[Introduction](https://www.kicksecure.com/wiki/Troubleshooting#Introduction)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[Introduction](https://www.kicksecure.com/wiki/Troubleshooting#Introduction)
Click = Copy
Copied to clipboard!
[Introduction](https://www.kicksecure.com/wiki/Troubleshooting#Introduction)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Introduction]Introduction[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Introduction]Introduction[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
Troubleshooting issues can be time intensive and success cannot be guaranteed. Some users expect Kicksecure to provide an easy experience. While the Kicksecure developers make every effort to meet user expectations, limited funding and human resources makes meeting these expectations impossible.
Even though problems emerge when using Kicksecure, the cause is most often unrelated to Kicksecure code. For example, users often report the same Kicksecure release worked on different hardware and/or with a different host operating system. Most software such as the host operating system or the virtualizer is developed by independent entities; this is the norm in Linux distributions. See Linux User Experience versus Commercial Operating Systems to learn more about these relationships, as well as organizational and funding issues in the Open Source ecosystem.
Essential General Troubleshooting Steps[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#Essential_General_Troubleshooting_Steps
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#Essential_General_Troubleshooting_Steps|Essential General Troubleshooting Steps]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#Essential_General_Troubleshooting_Steps|Essential General Troubleshooting Steps]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[Essential General Troubleshooting Steps](https://www.kicksecure.com/wiki/Troubleshooting#Essential_General_Troubleshooting_Steps)
Click = Copy
Copied to clipboard!
[Essential General Troubleshooting Steps](https://www.kicksecure.com/wiki/Troubleshooting#Essential_General_Troubleshooting_Steps)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[Essential General Troubleshooting Steps](https://www.kicksecure.com/wiki/Troubleshooting#Essential_General_Troubleshooting_Steps)
Click = Copy
Copied to clipboard!
[Essential General Troubleshooting Steps](https://www.kicksecure.com/wiki/Troubleshooting#Essential_General_Troubleshooting_Steps)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Essential_General_Troubleshooting_Steps]Essential General Troubleshooting Steps[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Essential_General_Troubleshooting_Steps]Essential General Troubleshooting Steps[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
![]() The following recommended steps will fix many startup, freezing or other unusual issues in Kicksecure. Skips steps that are no longer possible if a virtual machine is not bootable.
The following recommended steps will fix many startup, freezing or other unusual issues in Kicksecure. Skips steps that are no longer possible if a virtual machine is not bootable.
1. "Forget" about Kicksecure for a moment and imagine you had never heard of the platform. Test your host computer first.
2. Exclude basic hardware issues.
3. Ensure the virtual machine (VM) images have been imported into a supported virtualizer listed on the Download page.
4. Debian (based) Linux host operating system users only: The following command should not show any errors. [3]
Click = Copy Copied to clipboard! sudo dpkg-reconfigure -a
5. Debian (based) Linux host operating system users only: The following command should be silent and not show any errors or output at all. [3]
Click = Copy Copied to clipboard! sudo dpkg --configure -a
6. Debian (based) Linux host operating system users only: Next attempt to retrieve all available updates.
Click = Copy Copied to clipboard! sudo apt update
Click = Copy Copied to clipboard! sudo apt full-upgrade
7. Check for possible Low RAM Issues.
- Free up Additional Memory Resources.
- Also refer to Advice for Systems with Low RAM.
8. Virtualizer-specific troubleshooting.
9. Check if other VMs are functional, such as newly created ones or those from a different vendor.
- "Forget" about Kicksecure for a moment and imagine you had never heard of the platform. Test the virtualizer host software first.
- Try a VM other than Kicksecure such as Debian
bookworm. - If the issue persists, this means the root issue is not caused by Kicksecure, see: unspecific to Kicksecure. In this case, attempt to resolve the issue as per Self Support First Policy.
10. Check System Logs.
- Sometimes crashing or freezing issues are easier to detect by Watching Systemd Journal Log of Current Boot.
- Sometimes it is necessary to Check Systemd Journal Log of Previous Boot.
11. If a graphical environment (where one can use a computer mouse) is unavailable after booting, utilize a virtual console to acquire system logs.
- Recovery, Virtual Consoles.
- Check system logs of the previous boot (step 10).
12. Use recovery mode to acquire system logs.
- Boot in recovery mode.
- Check system logs of previous boot (step 10).
13. Use a chroot to acquire system logs.
If a virtual console is inaccessible and recovery mode is also broken, try using a chroot for recovery.
Low RAM Issues[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#Low_RAM_Issues
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#Low_RAM_Issues|Low RAM Issues]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#Low_RAM_Issues|Low RAM Issues]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[Low RAM Issues](https://www.kicksecure.com/wiki/Troubleshooting#Low_RAM_Issues)
Click = Copy
Copied to clipboard!
[Low RAM Issues](https://www.kicksecure.com/wiki/Troubleshooting#Low_RAM_Issues)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[Low RAM Issues](https://www.kicksecure.com/wiki/Troubleshooting#Low_RAM_Issues)
Click = Copy
Copied to clipboard!
[Low RAM Issues](https://www.kicksecure.com/wiki/Troubleshooting#Low_RAM_Issues)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Low_RAM_Issues]Low RAM Issues[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Low_RAM_Issues]Low RAM Issues[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
If insufficient RAM is available for Kicksecure VM they might become unusable. Low RAM issues in Kicksecure are commonly caused by:
- Unnecessary processes running and/or multi-tasking on the host OS.
- Multiple, open browser tabs.
- Unnecessary processes running in the Kicksecure VM.
- Allocating more RAM to the Kicksecure VM than is available; this prevents the VM from booting.
- Insufficient RAM allocated to the Kicksecure VM.
- Other non-Kicksecure VM running in parallel.
Insufficient RAM can cause multiple issues, but the most common effects include:
- Slow or unresponsive applications.
- The VM, mouse and/or keyboard freeze.
- Scrolling causes window staggers or jumps.
- Issues become worse when additional browser tabs or processes are spawned.
- Overall performance is poor.
See also: Advice for Systems with Low RAM.
Free up Additional Memory Resources[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#Free_up_Additional_Memory_Resources
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#Free_up_Additional_Memory_Resources|Free up Additional Memory Resources]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#Free_up_Additional_Memory_Resources|Free up Additional Memory Resources]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[Free up Additional Memory Resources](https://www.kicksecure.com/wiki/Troubleshooting#Free_up_Additional_Memory_Resources)
Click = Copy
Copied to clipboard!
[Free up Additional Memory Resources](https://www.kicksecure.com/wiki/Troubleshooting#Free_up_Additional_Memory_Resources)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[Free up Additional Memory Resources](https://www.kicksecure.com/wiki/Troubleshooting#Free_up_Additional_Memory_Resources)
Click = Copy
Copied to clipboard!
[Free up Additional Memory Resources](https://www.kicksecure.com/wiki/Troubleshooting#Free_up_Additional_Memory_Resources)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Free_up_Additional_Memory_Resources]Free up Additional Memory Resources[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Free_up_Additional_Memory_Resources]Free up Additional Memory Resources[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
If a VM needs additional memory, then free up resources and/or add more RAM to the VM:
- Terminate any non-essential processes on the host.
- Shut down any non-essential VM.
- Shut down and/or close non-essential processes and browser tabs in Kicksecure VM.
To add additional RAM to the Kicksecure VM, follow the platform-specific advice below.
KVM[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#KVM
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#KVM|KVM]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#KVM|KVM]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[KVM](https://www.kicksecure.com/wiki/Troubleshooting#KVM)
Click = Copy
Copied to clipboard!
[KVM](https://www.kicksecure.com/wiki/Troubleshooting#KVM)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[KVM](https://www.kicksecure.com/wiki/Troubleshooting#KVM)
Click = Copy
Copied to clipboard!
[KVM](https://www.kicksecure.com/wiki/Troubleshooting#KVM)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#KVM]KVM[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#KVM]KVM[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
1. Shutdown the virtual machine(s).
Click = Copy Copied to clipboard! virsh -c qemu:///system shutdown <vm_name>
2. Increase the maximum memory.
Click = Copy Copied to clipboard! virsh setmaxmem <vm_name> <memsize> --config
3. Set the actual memory.
Click = Copy Copied to clipboard! virsh setmem <vm_name> <memsize> --config
4. Restart the virtual machine(s).
Click = Copy Copied to clipboard! virsh -c qemu:///system start <vm_name>
Kicksecure-Qubes[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#Kicksecure-Qubes
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#Kicksecure-Qubes|Kicksecure-Qubes]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#Kicksecure-Qubes|Kicksecure-Qubes]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[Kicksecure-Qubes](https://www.kicksecure.com/wiki/Troubleshooting#Kicksecure-Qubes)
Click = Copy
Copied to clipboard!
[Kicksecure-Qubes](https://www.kicksecure.com/wiki/Troubleshooting#Kicksecure-Qubes)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[Kicksecure-Qubes](https://www.kicksecure.com/wiki/Troubleshooting#Kicksecure-Qubes)
Click = Copy
Copied to clipboard!
[Kicksecure-Qubes](https://www.kicksecure.com/wiki/Troubleshooting#Kicksecure-Qubes)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Kicksecure-Qubes]Kicksecure-Qubes[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Kicksecure-Qubes]Kicksecure-Qubes[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
Utilize Qube Manager:
Qube Manager→VM_name→Qubes settings→Advanced→Max memory:mem_size
VirtualBox[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#VirtualBox
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#VirtualBox|VirtualBox]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#VirtualBox|VirtualBox]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[VirtualBox](https://www.kicksecure.com/wiki/Troubleshooting#VirtualBox)
Click = Copy
Copied to clipboard!
[VirtualBox](https://www.kicksecure.com/wiki/Troubleshooting#VirtualBox)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[VirtualBox](https://www.kicksecure.com/wiki/Troubleshooting#VirtualBox)
Click = Copy
Copied to clipboard!
[VirtualBox](https://www.kicksecure.com/wiki/Troubleshooting#VirtualBox)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#VirtualBox]VirtualBox[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#VirtualBox]VirtualBox[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
- To add RAM in VirtualBox the VM must first be powered down.
Virtual machine→Menu→Settings→AdjustMemory slider→Hit: OK
See also: VirtualBox/Troubleshooting.
Generic Bug Reproduction[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#Generic_Bug_Reproduction
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#Generic_Bug_Reproduction|Generic Bug Reproduction]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#Generic_Bug_Reproduction|Generic Bug Reproduction]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[Generic Bug Reproduction](https://www.kicksecure.com/wiki/Troubleshooting#Generic_Bug_Reproduction)
Click = Copy
Copied to clipboard!
[Generic Bug Reproduction](https://www.kicksecure.com/wiki/Troubleshooting#Generic_Bug_Reproduction)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[Generic Bug Reproduction](https://www.kicksecure.com/wiki/Troubleshooting#Generic_Bug_Reproduction)
Click = Copy
Copied to clipboard!
[Generic Bug Reproduction](https://www.kicksecure.com/wiki/Troubleshooting#Generic_Bug_Reproduction)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Generic_Bug_Reproduction]Generic Bug Reproduction[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Generic_Bug_Reproduction]Generic Bug Reproduction[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
TODO
related: Generic Bug Reproduction
System Logs[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#System_Logs
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#System_Logs|System Logs]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#System_Logs|System Logs]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[System Logs](https://www.kicksecure.com/wiki/Troubleshooting#System_Logs)
Click = Copy
Copied to clipboard!
[System Logs](https://www.kicksecure.com/wiki/Troubleshooting#System_Logs)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[System Logs](https://www.kicksecure.com/wiki/Troubleshooting#System_Logs)
Click = Copy
Copied to clipboard!
[System Logs](https://www.kicksecure.com/wiki/Troubleshooting#System_Logs)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#System_Logs]System Logs[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#System_Logs]System Logs[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
Check Systemd Journal Log of Current Boot[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#Check_Systemd_Journal_Log_of_Current_Boot
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#Check_Systemd_Journal_Log_of_Current_Boot|Check Systemd Journal Log of Current Boot]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#Check_Systemd_Journal_Log_of_Current_Boot|Check Systemd Journal Log of Current Boot]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[Check Systemd Journal Log of Current Boot](https://www.kicksecure.com/wiki/Troubleshooting#Check_Systemd_Journal_Log_of_Current_Boot)
Click = Copy
Copied to clipboard!
[Check Systemd Journal Log of Current Boot](https://www.kicksecure.com/wiki/Troubleshooting#Check_Systemd_Journal_Log_of_Current_Boot)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[Check Systemd Journal Log of Current Boot](https://www.kicksecure.com/wiki/Troubleshooting#Check_Systemd_Journal_Log_of_Current_Boot)
Click = Copy
Copied to clipboard!
[Check Systemd Journal Log of Current Boot](https://www.kicksecure.com/wiki/Troubleshooting#Check_Systemd_Journal_Log_of_Current_Boot)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Check_Systemd_Journal_Log_of_Current_Boot]Check Systemd Journal Log of Current Boot[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Check_Systemd_Journal_Log_of_Current_Boot]Check Systemd Journal Log of Current Boot[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
To inspect the systemd journal log of the current boot, run.
Click = Copy Copied to clipboard! sudo journalctl -b
This command requires pressing arrow keys like ↑, ↓, ←, →, as well as PgUp and PgDn for scrolling.
For convenient reading of the log (until the command is issued), the log can be dumped to file. For example, the following command would write the log to file ~/systemd-log.
Click = Copy Copied to clipboard! sudo journalctl -b > ~/systemd-log
Use any available editor to read the log file, such as mousepad.
Click = Copy Copied to clipboard! mousepad ~/systemd-log
Watch Systemd Journal Log of Current Boot[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#Watch_Systemd_Journal_Log_of_Current_Boot
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#Watch_Systemd_Journal_Log_of_Current_Boot|Watch Systemd Journal Log of Current Boot]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#Watch_Systemd_Journal_Log_of_Current_Boot|Watch Systemd Journal Log of Current Boot]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[Watch Systemd Journal Log of Current Boot](https://www.kicksecure.com/wiki/Troubleshooting#Watch_Systemd_Journal_Log_of_Current_Boot)
Click = Copy
Copied to clipboard!
[Watch Systemd Journal Log of Current Boot](https://www.kicksecure.com/wiki/Troubleshooting#Watch_Systemd_Journal_Log_of_Current_Boot)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[Watch Systemd Journal Log of Current Boot](https://www.kicksecure.com/wiki/Troubleshooting#Watch_Systemd_Journal_Log_of_Current_Boot)
Click = Copy
Copied to clipboard!
[Watch Systemd Journal Log of Current Boot](https://www.kicksecure.com/wiki/Troubleshooting#Watch_Systemd_Journal_Log_of_Current_Boot)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Watch_Systemd_Journal_Log_of_Current_Boot]Watch Systemd Journal Log of Current Boot[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Watch_Systemd_Journal_Log_of_Current_Boot]Watch Systemd Journal Log of Current Boot[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
It is possible to to watch the systemd journal log as it is written.
Click = Copy Copied to clipboard! sudo journalctl -b -f
Check Systemd Journal Log of Previous Boot[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#Check_Systemd_Journal_Log_of_Previous_Boot
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#Check_Systemd_Journal_Log_of_Previous_Boot|Check Systemd Journal Log of Previous Boot]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#Check_Systemd_Journal_Log_of_Previous_Boot|Check Systemd Journal Log of Previous Boot]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[Check Systemd Journal Log of Previous Boot](https://www.kicksecure.com/wiki/Troubleshooting#Check_Systemd_Journal_Log_of_Previous_Boot)
Click = Copy
Copied to clipboard!
[Check Systemd Journal Log of Previous Boot](https://www.kicksecure.com/wiki/Troubleshooting#Check_Systemd_Journal_Log_of_Previous_Boot)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[Check Systemd Journal Log of Previous Boot](https://www.kicksecure.com/wiki/Troubleshooting#Check_Systemd_Journal_Log_of_Previous_Boot)
Click = Copy
Copied to clipboard!
[Check Systemd Journal Log of Previous Boot](https://www.kicksecure.com/wiki/Troubleshooting#Check_Systemd_Journal_Log_of_Previous_Boot)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Check_Systemd_Journal_Log_of_Previous_Boot]Check Systemd Journal Log of Previous Boot[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Check_Systemd_Journal_Log_of_Previous_Boot]Check Systemd Journal Log of Previous Boot[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
It is possible to inspect the systemd journal log of the previous boot.
Click = Copy Copied to clipboard! sudo journalctl -b -1
This command requires pressing arrow keys like ↑, ↓, ←, →, as well as PgUp and PgDn for scrolling.
For convenient reading of the log (until the command is issued), the log can be dumped to file. For example, the following command would write the log to file ~/systemd-log-previous.
Click = Copy Copied to clipboard! sudo journalctl -b -1 > ~/systemd-log-previous
Use any available editor to read the log file, such as mousepad.
Click = Copy Copied to clipboard! mousepad ~/systemd-log-previous
View List of Systemd Journal Logs[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#View_List_of_Systemd_Journal_Logs
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#View_List_of_Systemd_Journal_Logs|View List of Systemd Journal Logs]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#View_List_of_Systemd_Journal_Logs|View List of Systemd Journal Logs]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[View List of Systemd Journal Logs](https://www.kicksecure.com/wiki/Troubleshooting#View_List_of_Systemd_Journal_Logs)
Click = Copy
Copied to clipboard!
[View List of Systemd Journal Logs](https://www.kicksecure.com/wiki/Troubleshooting#View_List_of_Systemd_Journal_Logs)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[View List of Systemd Journal Logs](https://www.kicksecure.com/wiki/Troubleshooting#View_List_of_Systemd_Journal_Logs)
Click = Copy
Copied to clipboard!
[View List of Systemd Journal Logs](https://www.kicksecure.com/wiki/Troubleshooting#View_List_of_Systemd_Journal_Logs)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#View_List_of_Systemd_Journal_Logs]View List of Systemd Journal Logs[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#View_List_of_Systemd_Journal_Logs]View List of Systemd Journal Logs[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
Click = Copy Copied to clipboard! sudo journalctl --list-boots
Daemon Log View[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#Daemon_Log_View
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#Daemon_Log_View|Daemon Log View]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#Daemon_Log_View|Daemon Log View]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[Daemon Log View](https://www.kicksecure.com/wiki/Troubleshooting#Daemon_Log_View)
Click = Copy
Copied to clipboard!
[Daemon Log View](https://www.kicksecure.com/wiki/Troubleshooting#Daemon_Log_View)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[Daemon Log View](https://www.kicksecure.com/wiki/Troubleshooting#Daemon_Log_View)
Click = Copy
Copied to clipboard!
[Daemon Log View](https://www.kicksecure.com/wiki/Troubleshooting#Daemon_Log_View)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Daemon_Log_View]Daemon Log View[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Daemon_Log_View]Daemon Log View[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
To view the log of a specific systemd unit. Syntax:
(Replace unit-name with the actual name of the systemd unit.)
Click = Copy Copied to clipboard! sudo journalctl -b --no-pager -u unit-name
Example:
Click = Copy Copied to clipboard! sudo journalctl -b --no-pager -u sdwdate
Daemon Log Follow[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#Daemon_Log_Follow
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#Daemon_Log_Follow|Daemon Log Follow]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#Daemon_Log_Follow|Daemon Log Follow]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[Daemon Log Follow](https://www.kicksecure.com/wiki/Troubleshooting#Daemon_Log_Follow)
Click = Copy
Copied to clipboard!
[Daemon Log Follow](https://www.kicksecure.com/wiki/Troubleshooting#Daemon_Log_Follow)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[Daemon Log Follow](https://www.kicksecure.com/wiki/Troubleshooting#Daemon_Log_Follow)
Click = Copy
Copied to clipboard!
[Daemon Log Follow](https://www.kicksecure.com/wiki/Troubleshooting#Daemon_Log_Follow)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Daemon_Log_Follow]Daemon Log Follow[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Daemon_Log_Follow]Daemon Log Follow[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
To follow the log of a specific systemd unit. Syntax:
(Replace unit-name with the actual name of the systemd unit.)
Click = Copy Copied to clipboard! sudo journalctl -f -b --no-pager -u unit-name
Example:
Click = Copy Copied to clipboard! sudo journalctl -f -b --no-pager -u sdwdate
Daemon Status[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#Daemon_Status
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#Daemon_Status|Daemon Status]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#Daemon_Status|Daemon Status]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[Daemon Status](https://www.kicksecure.com/wiki/Troubleshooting#Daemon_Status)
Click = Copy
Copied to clipboard!
[Daemon Status](https://www.kicksecure.com/wiki/Troubleshooting#Daemon_Status)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[Daemon Status](https://www.kicksecure.com/wiki/Troubleshooting#Daemon_Status)
Click = Copy
Copied to clipboard!
[Daemon Status](https://www.kicksecure.com/wiki/Troubleshooting#Daemon_Status)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Daemon_Status]Daemon Status[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Daemon_Status]Daemon Status[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
To view the status of a specific systemd unit. Syntax:
(Replace unit-name with the actual name of the systemd unit.)
Click = Copy Copied to clipboard! sudo systemctl status --no-pager unit-name
Example:
Click = Copy Copied to clipboard! sudo systemctl status --no-pager sdwdate
Check Systemd Journal Log of Failed Boot[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#Check_Systemd_Journal_Log_of_Failed_Boot
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#Check_Systemd_Journal_Log_of_Failed_Boot|Check Systemd Journal Log of Failed Boot]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#Check_Systemd_Journal_Log_of_Failed_Boot|Check Systemd Journal Log of Failed Boot]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[Check Systemd Journal Log of Failed Boot](https://www.kicksecure.com/wiki/Troubleshooting#Check_Systemd_Journal_Log_of_Failed_Boot)
Click = Copy
Copied to clipboard!
[Check Systemd Journal Log of Failed Boot](https://www.kicksecure.com/wiki/Troubleshooting#Check_Systemd_Journal_Log_of_Failed_Boot)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[Check Systemd Journal Log of Failed Boot](https://www.kicksecure.com/wiki/Troubleshooting#Check_Systemd_Journal_Log_of_Failed_Boot)
Click = Copy
Copied to clipboard!
[Check Systemd Journal Log of Failed Boot](https://www.kicksecure.com/wiki/Troubleshooting#Check_Systemd_Journal_Log_of_Failed_Boot)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Check_Systemd_Journal_Log_of_Failed_Boot]Check Systemd Journal Log of Failed Boot[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Check_Systemd_Journal_Log_of_Failed_Boot]Check Systemd Journal Log of Failed Boot[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
An alternative to recovery mode might be virtual consoles, since they are an easier and more lightweight solution. A virtual console login might still be possible when the graphical user interface no longer starts.
Prerequisite knowledge: Virtual Consoles. Try to log in to a virtual console in a functional VM as an exercise. If that works, try a virtual console login in the broken VM.
If a virtual console is unavailable:
- Boot into Recovery Mode.
- Reboot into normal mode so a log for the failed boot will be written (if not previously enabled).
- Boot into recovery mode again.
- Check Systemd Journal Log of Previous Boot.
Permission Fix[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#Permission_Fix
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#Permission_Fix|Permission Fix]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#Permission_Fix|Permission Fix]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[Permission Fix](https://www.kicksecure.com/wiki/Troubleshooting#Permission_Fix)
Click = Copy
Copied to clipboard!
[Permission Fix](https://www.kicksecure.com/wiki/Troubleshooting#Permission_Fix)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[Permission Fix](https://www.kicksecure.com/wiki/Troubleshooting#Permission_Fix)
Click = Copy
Copied to clipboard!
[Permission Fix](https://www.kicksecure.com/wiki/Troubleshooting#Permission_Fix)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Permission_Fix]Permission Fix[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Permission_Fix]Permission Fix[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
![]() If something does not work, do not arbitrarily try to use sudo / root without any indication this is appropriate. Otherwise, this can negatively affect the correct user home folder permissions. See also: Safely Use Root Commands.
If something does not work, do not arbitrarily try to use sudo / root without any indication this is appropriate. Otherwise, this can negatively affect the correct user home folder permissions. See also: Safely Use Root Commands.
Open a terminal.
If you are using Kicksecure inside Qubes, complete the following steps.
Qubes App Launcher (blue/grey "Q") → Kicksecure App Qube (commonly named kicksecure) → Xfce Terminal
If you are using a graphical Kicksecure with Xfce, run.
Start Menu → Xfce Terminal
Click = Copy Copied to clipboard! sudo chown --recursive user:user /home/user
Hardware Issues[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#Hardware_Issues
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#Hardware_Issues|Hardware Issues]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#Hardware_Issues|Hardware Issues]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[Hardware Issues](https://www.kicksecure.com/wiki/Troubleshooting#Hardware_Issues)
Click = Copy
Copied to clipboard!
[Hardware Issues](https://www.kicksecure.com/wiki/Troubleshooting#Hardware_Issues)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[Hardware Issues](https://www.kicksecure.com/wiki/Troubleshooting#Hardware_Issues)
Click = Copy
Copied to clipboard!
[Hardware Issues](https://www.kicksecure.com/wiki/Troubleshooting#Hardware_Issues)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Hardware_Issues]Hardware Issues[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Hardware_Issues]Hardware Issues[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
General Recommendations[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#General_Recommendations
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#General_Recommendations|General Recommendations]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#General_Recommendations|General Recommendations]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[General Recommendations](https://www.kicksecure.com/wiki/Troubleshooting#General_Recommendations)
Click = Copy
Copied to clipboard!
[General Recommendations](https://www.kicksecure.com/wiki/Troubleshooting#General_Recommendations)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[General Recommendations](https://www.kicksecure.com/wiki/Troubleshooting#General_Recommendations)
Click = Copy
Copied to clipboard!
[General Recommendations](https://www.kicksecure.com/wiki/Troubleshooting#General_Recommendations)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#General_Recommendations]General Recommendations[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#General_Recommendations]General Recommendations[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
Rhetorical questions:
- When was the last time a qualified person disassembled your computer/notebook and removed dust from the fan and checked the cooling system of the CPU?
- How often should maintenance be performed?
- What is your CPU temperature under heavy system load?
- What is the room temperature where the computer is operating?
Recommendations:
- Ensure your computer or notebook has regular, proper maintenance.
- Monitor CPU temperature by utilizing relevant host operating system tools.
- Consider cooling the room where computers/notebooks operate.
- Better placement (more air space) around computers or notebooks can help.
- Consider a passive or active (notebook) cooling pad. [5]
- Run
memtest86+to rule out RAM problems.
None of these issues are related to Kicksecure. Therefore, please do not ask these questions in Kicksecure support channels (until there is a Kicksecure Host DVD available) as per Self Support First Policy.
memtest86+[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#memtest86.2B
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#memtest86.2B|memtest86+]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#memtest86.2B|memtest86+]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[memtest86+](https://www.kicksecure.com/wiki/Troubleshooting#memtest86.2B)
Click = Copy
Copied to clipboard!
[memtest86+](https://www.kicksecure.com/wiki/Troubleshooting#memtest86.2B)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[memtest86+](https://www.kicksecure.com/wiki/Troubleshooting#memtest86.2B)
Click = Copy
Copied to clipboard!
[memtest86+](https://www.kicksecure.com/wiki/Troubleshooting#memtest86.2B)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#memtest86.2B]memtest86+[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#memtest86.2B]memtest86+[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
1. Install the memtest86+ tool.
On Debian (based) hosts such as Kicksecure.
Install package(s) memtest86+ following these instructions
1 Platform specific notice.
- Kicksecure: No special notice.
- Kicksecure-Qubes: In Template.
2 Update the package lists and upgrade the system![]() .
.
Click = Copy Copied to clipboard! sudo apt update && sudo apt full-upgrade
3 Install the memtest86+ package(s).
Using apt command line --no-install-recommends option![]() is in most cases optional.
is in most cases optional.
Click = Copy Copied to clipboard! sudo apt install --no-install-recommends memtest86+
4 Platform specific notice.
- Kicksecure: No special notice.
- Kicksecure-Qubes: Shut down Template and restart App Qubes based on it as per Qubes Template Modification
 .
.
5 Done.
The procedure of installing package(s) memtest86+ is complete.
For other host operating systems, refer to memtest86+ upstream documentation.
2. Reboot.
3. Start memtest86+ from (grub) boot menu.
4. Keep memtest86+ running for a significant period.
This should be run for as long as practically possible; for example, ideally overnight or for 8+ hours.
5. Check the memtest86+ output.
If there are any issues, red error messages appear in the middle of the screen.
6. Done.
The memory test is complete.
If memtest86+ identified any issues, these can manifest in various ways such as system crashes at random times. In such cases, the only likely solution is replacing the faulty hardware (RAM banks). [6]
Hard Drive Health Check[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#Hard_Drive_Health_Check
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#Hard_Drive_Health_Check|Hard Drive Health Check]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#Hard_Drive_Health_Check|Hard Drive Health Check]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[Hard Drive Health Check](https://www.kicksecure.com/wiki/Troubleshooting#Hard_Drive_Health_Check)
Click = Copy
Copied to clipboard!
[Hard Drive Health Check](https://www.kicksecure.com/wiki/Troubleshooting#Hard_Drive_Health_Check)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[Hard Drive Health Check](https://www.kicksecure.com/wiki/Troubleshooting#Hard_Drive_Health_Check)
Click = Copy
Copied to clipboard!
[Hard Drive Health Check](https://www.kicksecure.com/wiki/Troubleshooting#Hard_Drive_Health_Check)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Hard_Drive_Health_Check]Hard Drive Health Check[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Hard_Drive_Health_Check]Hard Drive Health Check[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
TODO: document
also known as S.M.A.R.T
- smartmontools
- gsmartcontrol
- smart-notifier
- nvme-cli
- package: gnome-disk-utility run: gnome-disks
- https://packages.debian.org/bookworm/lm-sensors

- https://packages.debian.org/bookworm/plasma-disks

- https://packages.debian.org/bookworm/psensor

- https://wiki.debian.org/SystemMonitoring

See Also[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#See_Also
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#See_Also|See Also]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#See_Also|See Also]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[See Also](https://www.kicksecure.com/wiki/Troubleshooting#See_Also)
Click = Copy
Copied to clipboard!
[See Also](https://www.kicksecure.com/wiki/Troubleshooting#See_Also)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[See Also](https://www.kicksecure.com/wiki/Troubleshooting#See_Also)
Click = Copy
Copied to clipboard!
[See Also](https://www.kicksecure.com/wiki/Troubleshooting#See_Also)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#See_Also]See Also[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#See_Also]See Also[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
- Advice for Systems with Low RAM
- VirtualBox Troubleshooting
- KVM Troubleshooting
- Recovery Mode
- System Recovery using SysRq Key
- Core Dumps
Footnotes[edit]
Copy or share this direct link!
Click = Copy
Copied to clipboard!
https://www.kicksecure.com/wiki/Troubleshooting#Footnotes
Click below ↴ = Copy to Clipboard
 Click = Copy
Copied to clipboard!
[[Troubleshooting#Footnotes|Footnotes]]
Click = Copy
Copied to clipboard!
[[Troubleshooting#Footnotes|Footnotes]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[Footnotes](https://www.kicksecure.com/wiki/Troubleshooting#Footnotes)
Click = Copy
Copied to clipboard!
[Footnotes](https://www.kicksecure.com/wiki/Troubleshooting#Footnotes)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[Footnotes](https://www.kicksecure.com/wiki/Troubleshooting#Footnotes)
Click = Copy
Copied to clipboard!
[Footnotes](https://www.kicksecure.com/wiki/Troubleshooting#Footnotes)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Footnotes]Footnotes[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting#Footnotes]Footnotes[/url]
Copy as phpBB
Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
- ↑
- Question: Why does it happen with Kicksecure ISO but not with Debian or some other ISO?
- Answer: Not sure. Maybe a race condition. Or perhaps the premise might be wrong. A web search for this error message shows running Ubuntu and attempting to flash a Windows 10 ISO using KDE ISO Image Writer

failed. Also flashing KDE Neon failed

. This error seems to be reproducible with many Linux distributions. It is probably only possible for the KDE ISO Image Writer developers to fix this bug. There is probably nothing that the Kicksecure ISO could do better.
- Answer: Not sure. Maybe a race condition. Or perhaps the premise might be wrong. A web search for this error message shows running Ubuntu and attempting to flash a Windows 10 ISO using KDE ISO Image Writer

- Question: Why does it happen with Kicksecure ISO but not with Debian or some other ISO?
- ↑
This procedure was useful for Kicksecure for Qubes R3.2 users, although the Qubes bug report is now resolved: https://github.com/QubesOS/qubes-issues/issues/2141

- ↑ Jump up to: 3.0 3.1 This process can be lengthy.
- ↑
"user support template": https://forums.whonix.org/t/workstation-keeps-freezing/7693/6

- ↑ Perform thorough research beforehand.
- ↑ RAM bank warranties may apply.
 Click = Copy
Copied to clipboard!
[[Troubleshooting|Troubleshooting - Kicksecure]]
Click = Copy
Copied to clipboard!
[[Troubleshooting|Troubleshooting - Kicksecure]]
Copy as Wikitext
 Click = Copy
Copied to clipboard!
[Troubleshooting - Kicksecure](https://www.kicksecure.com/wiki/Troubleshooting)
Click = Copy
Copied to clipboard!
[Troubleshooting - Kicksecure](https://www.kicksecure.com/wiki/Troubleshooting)
for Discourse, reddit, GitHub
 Click = Copy
Copied to clipboard!
[Troubleshooting - Kicksecure](https://www.kicksecure.com/wiki/Troubleshooting)
Click = Copy
Copied to clipboard!
[Troubleshooting - Kicksecure](https://www.kicksecure.com/wiki/Troubleshooting)
Copy as Markdown
 Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting]Troubleshooting - Kicksecure[/url]
Click = Copy
Copied to clipboard!
[url=https://www.kicksecure.com/wiki/Troubleshooting]Troubleshooting - Kicksecure[/url]
Copy as phpBB Click below ↴ = Open social URL with share data








 We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.
We don't use embedded scripts
This share button is completely self-hosted by this webserver. No scripts from any of the social networks are embedded on this webserver. See also
Social Share Button.

We believe security software like Kicksecure needs to remain Open Source and independent. Would you help sustain and grow the project? Learn more about our 12 year success story and maybe DONATE!